C.U.: Computer Underground
Canada
Haxoft (developer and publisher)
Released as freeware in 1993 for DOS
Date Started: 26 July 2025
Date Ended: 26 July 2025
Total Hours: 2
Difficulty: Very Easy-Easy (1.5/5)
Final Rating: (to come later)
Ranking at time of posting: (to come later)
Whether a CRPG requires combat is an age-old debate, and into it wades C.U.: Computer Underground from Toronto-based author Jeff Marlow. No one dies in this game, but their computer systems do get trashed. The character has a skill level and uncorrupted megabytes of storage space instead of hit points. He battles corporate servers and other hackers.
The game might be fun, and it might be an interesting entry into this debate, if it offered any strategy or gave any insight into actual hacking. But it's far too trite and simple, and its use of technical terms makes little sense.
 |
| The font makes me think that C.U. was originally a different kind of game. |
"Character creation" consists only of a hacker handle. Right away, the game misses some opportunities to explore different types of hackers and give them different goals and skills, or at least to offer a tradeoff between skill and money for a new character.
The character starts at experience level 1 (and therefore a hard drive capacity of 10 megabytes), $150 cash, a communications program called BiteComm v. 0.28, no hacking program, no virus shield, a generic virus, a programmable calculator, and backup media by abacus.
 |
| My items and options at Level 7. |
The player's options each round are to:
- Go to "Wired World" to buy or sell computers, backup media, virus shields, hack programs, or communications programs. Each item has an intrinsic level. The computer determines what level of software you can run.
- Crack a BBS, corporate system, or government system.
- Battle with another cracker and try to crash his machine.
- Attempt to hack a bank and steal money.
- Restore lost megabytes of hard disk space (i.e., heal).
- Spend $100 to gather intelligence about another cracker.
 |
| I hope when the time comes, I can overcome his programmable calculator. |
Without much effort, you can mentally plug in the analogs for a fantasy RPG. As you successfully crash systems and defeat other hackers, you (somehow) earn money, which lets you buy better equipment, which lets you try the next level.
 |
| The list of computers riffs on real machines. |
The game is a little tough at the beginning. Your $150 won't buy even the cheapest hacking program, so the only things you can do that are effective are: a) Battle with the worst cracker, Space Cadet, and earn a few hundred dollars crashing his system, or b) sell your backup program to earn enough to buy the worst hacking program (Trial & Error for $175), then hack the lowest-level entity (Lamer Lounge).
Alternatively, you could try to hack the bank. You have a 1 in 3 chance of getting $999 or less, a 1 in 6 chance of getting $1,000 to $1,999, and a 1 in 8 chance of getting more than $2,000. You have to choose which option you're going for. None of the odds are very good, and if you lose, you often lose your computer, which effectively ends the game. The odds never change. It's not worth the risk for higher-level characters, but a Level 1 player might as well take the chance and start afresh if he loses.
 |
| The odds, while poor, are probably better than in real life. |
Hacking corporate and government systems is a little fun. You have options like a Dungeon BBS, the power grid, the local pizza shop, a hospital's I.C.U., YBM Computers, and a couple of federal agencies. Your hacking program level has to be equal to the security system of the target computer. If it is, you end up playing a little game of Concentration in which you have to match 8 pairs of cards: user lists, texts, top secret, public files, data files, private files, system files, and system logs. You click on two cards, and if they match, they turn into smiley faces. If not, they turn back over, and you have to try again, remembering where you saw the various options. You're doing all of this against a clock that starts at a generous 90 seconds for Lamer Lounge and goes down to 15 seconds for the federal mainframe. (Failure means getting caught, paying a fine, and perhaps losing your computer or hacking program.) Fortunately, I'm very good at Concentration.
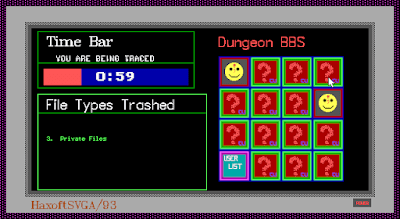 |
| In order to trash file types, I apparently have to find them two at a time. |
Battles with other hackers are less interesting. Your "megs" are paired against his, and you can do a direct attack with "trash megs" or send a virus over (i.e., cast a spell). Either option gives him the chance to retaliate (his level and your communications and antivirus programs determine these odds). You can try to restore megs from your backup media in the middle of battle, with success dependent upon its quality.
 |
| I send a virus to Myssing Lynk. |
Any person ignorant of computers would get some weird ideas from C.U.:
- Your skill with computers determines your hard drive storage capacity.
- When you transmit a virus to another computer, you lose it from your own machine and have to buy a new one.
- Different types of files can only be deleted in pairs.
- Causing corporate systems to crash somehow transmits money to your bank account.
- "Hacking" is all about directly destroying hard drive capacity on the target machines. That is exclusively what viruses do.
- Computer programs exist on a strict hierarchy from bad to good rather than specializing in certain things.
- Hacking programs are sold at commercial computer stores.
I can't tell you how forward I'm looking to the various "well, actually" comments on each of these bullet points.
Seriously, though, the game is mostly a lot of missed opportunities. What if each target system was a bit different and needed different types of programs and strategies to overcome? What if you had roleplaying options involving things like transmitting money to either charities or your own account? What if instead of playing Concentration, you had to type some actual commands, maybe learn a bit about actual hacking? (Marlow says in the notes that he doesn't actually encourage hacking, so I suppose that's why everything is abstract.) What if you could pay for training? What if instead of getting dossiers on other hackers, you could get dossiers on targets and then use them to guess passwords? There are a lot of ways to expand upon this rather plain template to make it more interesting.
 |
| The price of failure. |
But it is an example of an RPG-like game in which nothing dies, which is pretty rare for the genre. I don't think I've played a game that fit that description since
SoccerStar (1989), and I rejected that one as an RPG.
 |
| . . . and a high-level position in DOGE. |
Once you have the best computer (Moon Workstation) and the best hacking program (Code Jaws 8.0), you can try to hack the U.S. government mainframe. You only have 15 seconds to match the eight pairs of cards. If successful, the game proclaims you the "best hacker in the world," which qualifies you for a job at Haxoft.
 |
| It's a magical place. |
A secondary goal would be to beat the best hacker, King Krasher, but that's not hard as long as you've leveled up enough to beat his "total megs" (200). You earn $2,000 for destroying his system.
The game uses a mostly-mouse interface, which I find a little annoying. There's no reason that every screen couldn't have numbered items. Obviously, the mouse is the right tool for the Concentration mini-game. There's no sound, and graphics are minimal.
The equivalent of
C.U. on the fantasy side would be an all-menu game in which you fight repeated battles and slowly upgrade equipment as you make money—something like
Darkwood (1992) for the Mac, for instance. That's fitting, because I gave
Darkwood an 18 on the GIMLET, and I give
C.U. a 17. It's an interesting idea that needed a little more complexity. At least it's not a German
Ultima clone.
****
Please note that I added a supplement to my last entry on
The Ormus Saga II, wrapping up that game.












The bank hacking and gather intelligence about another hacker make this a little bit more than just "the usual fantasy RPG except in a computer setting), but it's sad that RPGs didn't really seem to adapt ideas from 1984's Core War. I'm not even sure how many RPGs offer some kind of scripting/customizable combat. FF12's Gambit system comes to mind, and some later games do it (Dragon Age, Dragon's Dogma, Unicorn Overlord come to mind), but "Computer Hacking in CRPGs" has to be one of the most disappointing implementations of a good concept in the entire genre.
ReplyDeleteAlso, let that be a life lesson to all: Investing in an ergonomic keyboard and vertical mouse will save you from having to right elderly female terrorists on your vacation!
DeleteWouldn't a notepad make a better backup medium than an abacus?
ReplyDeleteSomebody got a little carried away with Borland's fonts. A good theme, but it's a pity that the mechanics are such a let down.
Funny to see the computer prices. My "Amigo 1000" cost more than my "486 Screamer" did, when new.
The price is just about right for what we paid for our family's "Pendulum 5," too.
DeleteMeanwhile, a "Coleekho ADA-M" is somehow MORE valuable than a "Commie 64", and a "Pendulum 5" is only slightly more expensive than a "486 Screamer", when in 1993 it should have been ridiculously expensive and not widely available.
DeleteAlso, an abacus is not even remotely capable of data storage and/or backup. A Scrabble board can store more data than an abacus!
Decker from 2002 is a roguelike that simulates hacking with a bit more depth. On the flipside, it's also even closer to being a reskin of a typical fantasy roguelike.
ReplyDeleteAlso Matrix segments in Shadowrun (Sega Genesis version) at least try to look different and are fairly involved (the game is generally a PC RPG in its ethos, and a pretty good one at that, that somehow ended up on a console).
I was hoping someone would mention Decker, which is great. My understanding is that it cribs pretty heavily from Shadowrun, too.
DeleteHm, I wonder if this is the progenitor of numerous 90's and 00's menu-driven games about hackers (and drug dealers, I think?). I remember at least several of them for DOS and Windows 95, though without names. I don't think any of them should really qualify as RPGs, though.
ReplyDeleteAs for more advanced hacking games, there is Uplink, though when I tried it, I was still disappointed.
The recent HeistGeist has a decent hacking mini-game, which is not at all like real hacking, but at least is fun.
Quazatron, a ZX Spectrum game about battling robots with your own robot where you could capture pieces of enemies, had a somewhat interesting hacking mini-game, too (you could either shoot or hack other robots). You had to "capture" a common set of nodes by placing "claims" on them, while enemy did the same. I don't remember all details, but it was a bit too easy, but still fun. I always wanted to make an RPG remake of that game. Somebody beat me to it by writing the open-source FreedroidRPG (which, I guess, CRPGAddict gets to try when he gets to 2023, when 1.0 version was released), but as far as I remember, it didn't have the mini-game (but I played in WAAAAY before 1.0, so maybe I should revisit ti).
Sid Meier's Covert Action featured "wire tapping" mini-game, which I consider one of the best mini-games ever designed. It presented you with a board full of logic gates and "current" running through it. You had to move the gates around, so that current powered all "tap nodes", and never touched "alarm nodes". It could easily be adapted into a hacking mini-game in another game. I would gladly take it over the boring "password guessing" in Fallout 3 (not that Fallout 3 exists, of course).
That Quazatron minigame sounds a lot like Paradroid. Turns out it started as a port of that game.
DeleteI keep meaning to code a remake of that covert action minigame. Agree that it’s all nicely done and an interesting puzzle, especially on the harder difficulties
DeleteWhen I read that hacking here consists in matching pairs of cards, I also thought of the minigame in Paradroid - part of a C64 classic I've still fired up from time to time many years later - as an alternative that would seem more fitting.
DeleteTalking about other examples of hacking minigames, if we are not limiting it to CRPGs, the battles against ICE and AIs in Neuromancer come to mind (it was covered on The Adventurers Guild back when it was still a solo project run by The Trickster and called The Adventure Gamer).
Hey, Deano! I made a genetic-algorithm based generator of puzzles for this mini-game a while ago (like, 10-15 years ago). I guess we can cooperate :) I mean, it's actually probably a stupidly costly approach for generating puzzles, yeah, but I wanted to play with GAs at that point.
DeleteThere is a bunch of games that kind of recreate the idea, though. I personally played "Make It True" (sadly no longer available on Google Play, but it's still on Apple Store, if you have iPhone, and you can install it on Android from other sources). The quick search also shows "Logic Gates" and "Logica Game" on Android, and much more advanced gates-based games on PC/web, like "Turing Complete" and "NANDgame". Also, there is "Bomb Squad Academy", which is more like Covert Action, and less like circuit design, but I found it has too tight timers for my liking.
GAs - nice! I did my final year project at uni on GAs for scouting in a Civ style game.
DeleteMy idea to generate the puzzles is more algorithmic. First randomly pick chips for each slot (from a pool which increases with difficulty, maybe have this be weighted), then see if that generates any alarm - if so, then trace through the path for that and swap a chip out with one which inverts the output for that path (have a table of replacement chips which you can randomly pick from). Then see how many successes you have. If not enough, then pick one of the non-succeeding paths and again replace a chip on that path to make it a success.
Once that's all done, you then swap random chips a certain number of times, based on difficulty (with some randomness). Each step make sure you don't trigger an alarm, or at least not enough alarms to fail the puzzle. If the random swap does, then undo it and pick another random swap. Keep a track of how many times you fail to swap and if it hits a threshold, then just abandon that puzzle set and create a new one.
Potentially that should work, but there is a risk that it'll generate a whole load of non-working puzzles which means it'll take a while to generate one that works. But any puzzle given the player would be completable.
That said, I'd love to add more features to the puzzle. Maybe instead of just the end spaces being blanks, successes and alarms, you might have to turn on a particular end chip in addition to a number of other successes. Or you could have a 'current limit' where you can't have the current going through too many chips. Or you could have faulty chips, where the logic on the chip doesn't work which you'll have to figure out through the traces.
Lots of potential ways to mess with the formula!
> then trace through the path for that and swap a chip out with one which inverts the output for that path
DeleteI'm not sure that would work, because swapping a chip to invert the output might also affect other outputs, and it worst case you can end up with endless loop where two paths compete for the same chip. You can add the restriction that other outputs should not be affected, but this is impossible in some cases - you need to replace more than 1 chip at the same time.
I tried to think of an algorithmic approach, but I feel I'm too stupid for that. I wonder how the original generation worked. But I think it's not bug-free, because I saw a post somewhere about it.
As for the second part of the generation ("breaking" the working scheme) it's also exactly what I did!
Oh Paradroid! Thanks for the memories!
DeleteI'm trying to think if other hacking minigames- Mass Effect had one?
Y0U 5H0U1D H4V3 Wr1773N 7H15 3N7rY 1N 1337 5P34K
ReplyDelete7h47 w0uld h4v3 b33n 3xh4u571n6.
Delete7h323 423 4 num832 0f 1337 5p34k 724n5147025 0u7 7h323 70 5p33d up 7h3 p20c355. n07 700 m3n710n, 1 837 7h3 41 c4n d0 17 45 w311!
Deleted0n7 3v3r r34d )(0m357uck
Deleten00b 7r4n51@t0r
DeleteWould you count Bugs and Drugs as involving combat? It had you "fight" the diseases, in terms of your immune system fighting them off. You could die though. In terms of unquestionable cRPGs where no one dies, I'm pretty sure that defeat in Pokemon is non-lethal, and that there are other similar cases (possibly also aimed at kids), but maybe nothing you've reached yet.
ReplyDeleteMichael Brough's 868-HACK (now being remade) is skinned as about hacking but is maybe even less representational of it than this--you move your avatar around and zap various monsters that represent security systems. Also though it's considered a mini-roguelike, it'd fail your RPG criteria because character development is only through upgrades.
I sometimes talk about an idea for an RPG based on getting out the vote, where combat is talking to people to try to convert them, hit points represent your will to proceed, different argumentative strategies are weapons, mana points are cellphone burner minutes you can use to call HQ for analyses and other special effects, and money is... money. I have now talked about it again.
(Converted voters giving you money and sometimes new arguments makes more sense here than in RPGs. This was also true of my idea for making tower defense nonviolent, which was about designing a mall so the people walking through it would see the most effective advertisements.)
BND is a weird halfway example. You are technically in "combat" against a virus, even though it doesn't make a lot of sense.
DeleteI like your idea, but I think it sounds more like a political sim (is that a genre) than an RPG. My problem with any RPG that doesn't involve combat is that I tend to regard it as a rare curio. If a LOT of games spawned in that direction, I think we'd have to call them something else.
Actually I really like that idea - you could make it into a roguelike/run-based game that takes advantage of the spatiality of RPGs by focusing it on canvassing/door knocking. That way there are built in organic constraints and decisions on which turf to go to (suburbs have richer people but are spread further apart, e.g.) and you could have an upgrade cycle after each run allowing you to bank money into better materials, polling/messaging research to improve your targeting and the effectiveness of your persuasion, etc.
DeleteMy original idea was absolutely a canvassing/door-knocking roguelike. Chet, there are definitely political sims though I don't know if they're a genre so much as a theme (like fantasy games). My original imaginary game idea was a blatant re-skin of combat mechanics--like instead of "TROLLS are vulnerable to ELECTRICITY so I wield MJOLNIR" it would be "HIPSTERS are persuadable by IDEALISM so I prepare the ARGUMENT ABOUT MEDICARE FOR ALL" with very similar underlying mechanics. Not much risk of it becoming more than a rare curio!
DeleteWell, actually ;) your paragraph about the missed opportunities illustrates quite nicely why I think you should try your hand on your own game design, whether on the computer or tabletop.
ReplyDeleteWith the 'custom everything' approach of the internet I was able to put together prototypes of card/boardgames without spending much money.
"I can't tell you how forward I'm looking to the various "well, actually" comments on each of these bullet points."
ReplyDeleteWell actually, that cracked me up, sir!
I didn't get any! I was so sure.
DeleteYour scrying orb has been traced. The night watch kick down your door and they TAKE YOUR HORSE.
ReplyDeleteWhen you get it back your saddle is gone. Legal fees cost you 1850 copper pieces.
§ CLICK THE MOUSE §